This post is inspired by a lot of questions I get about emails:
Hey I got this strange email the other day…
There are different mails that the security community considers suspicious. There are:
- phishing mails that want to steal your password
- scam mails that want you to pay money
- ransom mails that blackmail you into paying money
- spam mails which make you click on links
- malware mails which make you install a virus
- test mails that are sometimes used to collect information about the address owner
- and even more variations…
There are some misunderstandings about emails, and this is one reason that many people fall for them.
Misunderstanding email adresses
Often people compare email addresses with their postbox. Emails carry their name (davide.bove@_.com), and can only be read by the owner. A letter is always addressed to you, it contains a street and a city name. We expect that people know about us when both our name and our address is correct.
Emails are different. First of all, they are shorter. They often contain only your fullname. The mail “firstname.lastname” is so common that you only need to know the name to get the address. This means that email adresses are not private. You can hide your full name by using a different name like “donaldduck1989@_.com”, but the address is still easy to guess. Only few people use random mail handles. Emails need to be easily recognizable and easy to communicate, so they are short and memorable.
Emails are not letters. They are not difficult to send at scale. How much do you think it takes to send 1 million emails? And how much to send 1 million letters? Mailgun, a service to send automated emails, offers to send up to 15,000,000 emails per hour. That is 4 minutes to send a million mails, while even the most efficient mail service would take 1-3 days to deliver the same amount of letters, if you limited your destination to one city.
Emails are easy to fake. Anyone can craft an email that will show you “Bill Gates” or “Police Department XYZ” as the sender. This is nothing only hackers can do, you can specify whatever name you want in your own mail software.
Even worse: You can change the origin email, such that you can send someone a mail coming from “billgates@microsoft.com”. This is actually the same as with physical letters. You can write whatever you want on the envelope. You can send it from your local post office, or if you want to be less trackable, you can drive for an hour and bring it to a more distant post office. The tecnical equivalent is your IP address, which tells a recipient where the mail was sent from.
Fake emails are easy to create and hard to detect. This is why you need to be suspicious of any email you receive. And this is objectively hard. No one likes to focus on the authenticity of every email they get. It is simply against the human nature, and this is what criminals exploit.
Red flags
I want to give you some personal examples of red flags that make any email suspicious to me. Suspicious mails are handled with much attention to details, while “not suspicious” mails is where the attention is gone. This list should be applied both to work and private emails.
Please note: I am an expert in the field and I was tricked multiple times into interacting with fake and malicious emails. If you are a victim of any email-related fraud, do not blame yourself. This s**t happens every day and to almost everyone. But you can learn from mistakes and react better the next time it happens.
Unknown sender
This should be obvious. There are people and companies that you have never interacted with, and now they are writing to you. Most spam mails fall into this category. I think this is an obvious red flag.
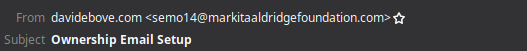
Example
You can see the name says “davidebove.com”, but the email was sent from a very suspicious address.
What to do
Check the domain part of the email (this is the part after the @ symbol). Have you ever heard of the website? If not, ignore or delete the email.
Links
Whenever there is a hyperlink in the mail, I get suspicious. You get a myriad of mails with clickable links, and every link can lead you to a potential danger. Most of them are harmless, but you can never tell.
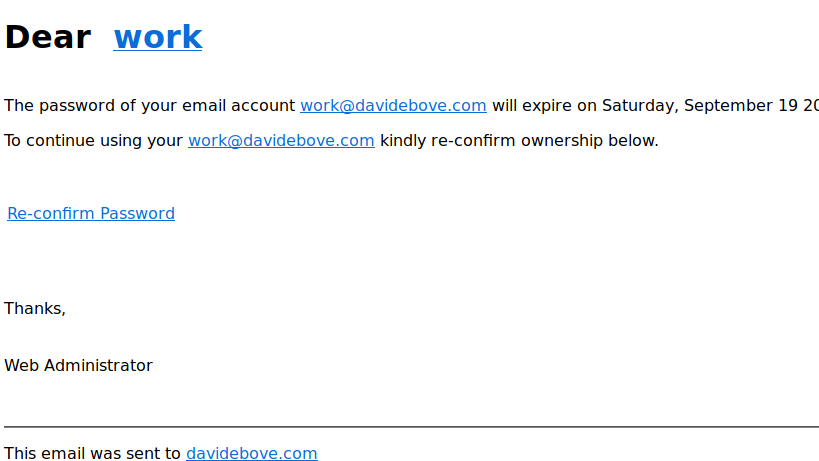
Example
A mail with a number of links that urges me to enter my password into a website.
What to do
Before you click on any links, take the mouse pointer and put it on top of the link. In most cases, you are shown where this link leads to. If you have no idea what you are reading, do not click on the link.
BUT: the mail is telling you that there is an important message? That you absolutely need to open the link? Well then, open your Internet browser and manually type in the page you want to look at. On mobile, directly open the corresponding app.

Attachments
Attachment most often fall into the category malware mails. The mail urges you to open the attachment, because “here is your bill” for an article you did not order or “hey look at this sexy picture of myself”. In my experience, Word/Excel documents are the most popular attachments where viruses are hidden. But recognizing what type of attachment you received is next to impossible, even for IT people.
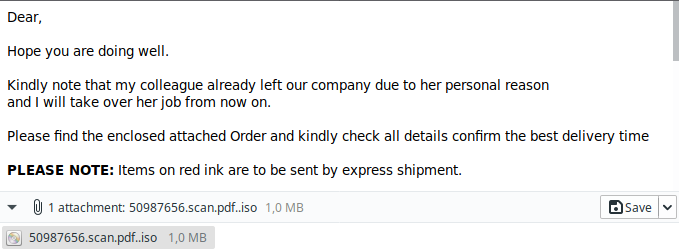
Example
As you can see, the email contains clear instructions to open the attachment (“mind the red ink”). In this example, the attachment is not even a document, but an executable program, a Windows .exe program. If you open it, a virus is installed.
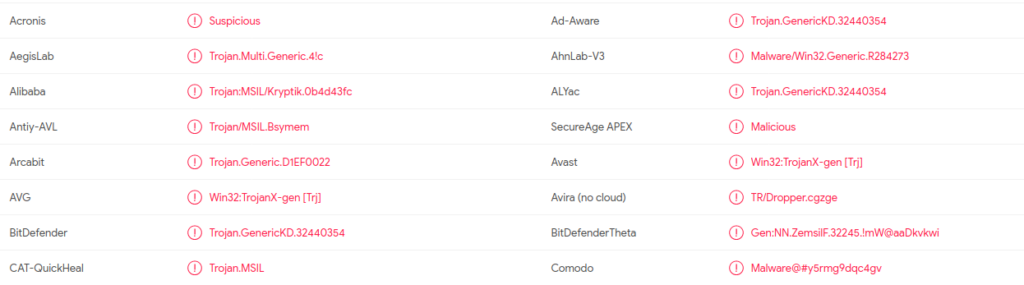
Curious about what it does? Virustotal is a service that scans a file with 71 antivirus programs. 54 programs detected this file as malicious:
What to do
Never open an attachment if you did not expect to receive something. If you get an unexpected attachment from your coworker, get suspicious and check for other red flags before you open or save an attachment.
Content
The content is often an indicator that something is shady. The language is strange, full of errors, not the language you would expect from the recipient or simply not very typical. Whenever the message sounds too good to be true, it always is.
Examples
I got my fair share of shady, funny and really stupid spam mails. The following one falls into the category spam. An unexpected message from hacked email accounts with a link.
Another typical spam mail contains stories about people with money that want you to help them. The stories are sometimes entertaining, but of course no one would ever gift money to a random stranger.
From the ransom mail category I have a nice example of mails that might scare some people into paying. Note that this is a totally impersonal and shady email, and you most certainly do not need to fear any consequences.
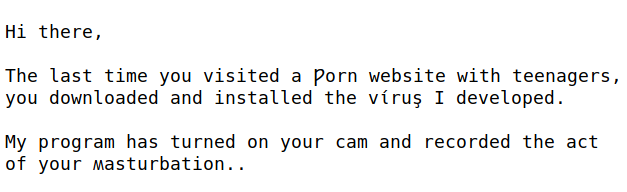
These mails are spread all over the Internet, and it’s not uncommon that some recipient might feel addressed of the accused actions. You have nothing to fear here, most of the time.
What to do
Delete the mail. If the mail is suspicious to you, there will be no consequences of simply ignoring and deleting it. If you are not sure if your coworker really sent you that strange email, try to ask them in person or give them a call.
There are more indicators that might raise some suspicions. I once received an email from a superior with a link, but with a clear request and not that unusual. It was signed with the real name of the superior and the text:
--
Sent from my iPhoneSomeone thought that was a good idea, Apple phones are wide-spread. But the superior in question was a little bit paranoid, so never owned a smartphone. This revealed the mail to be a fake.
Conclusion
Detecting fake emails is hard. There are far more dangerous situations that are not discussed here, but you might encounter it. The best things you can do:
- if you have a spam filter in your email software, enable it. It helps.
- Never trust emails.
- Check links before clicking.
- Never open attachments you were not expecting.
- If something seems fishy, it probably is.
- If you are suspicious but think the email might be important, contact the sender through other channels. Speak to your supervisor, call your bank or ask for the opinion of others before interacting with the email.



Be First to Comment