Recently, my workplace provided interested employees with a YubiKey, a small security key that provides “Two-Factor Authentication†to computers and mobile devices. It is not the first YubiKey I own, so my first thought was:
Great! Now, what am I using this for?
Since it offers more features than people think, I want to present several use-cases of a YubiKey here.
What is a YubiKey?
A YubiKey is a small physical device that provides an extra layer of security for your online accounts and digital information. It acts like a digital key that you can plug into your computer or mobile device to verify your identity during login.
By requiring this physical token in addition to your password, a YubiKey makes it significantly harder for unauthorized users to access your accounts and your data.
You may ask where the additional security comes from? Allow me to introduce the concept of Multi-Factor Authentication.
When you log into an account, you usually require a username and a password. The password is the secret which is used to identify yourself. Only you should know the password, so it can be only you logging in. This is what security professionals call a “factorâ€.
Now, it is known that “hackers†might get your password, either by “hacking†you or by “hacking†the services you use. Either way, your password is not always secret, and it may not even be your fault that someone else has it.
To avoid any other people logging into your accounts using your password, many services provide a method to register a second factor. But it would not be helpful to use a second password because the hackers could get access to it in the same way. So, a secure second factor needs to be either:
- Something you are, or
- Something you own.
The first type is determined by physical attributes of yourself, and you often need appropriate sensors to measure them. Therefore, most “biometric†sensors we use daily are either fingerprint sensors (e.g., built into phones) or face scanners. A hacker cannot simply copy your fingerprint, therefore providing biometrics as a second factor can be actually pretty safe.
For the second type, you require a physical object that a hacker cannot simply download from a database. For example, your phone is a second factor that you probably always carry with you. Or….a YubiKey! With a phone, you can receive a message through an app, or receive a text by SMS to authenticate yourself. With a YubiKey or similar hardware keys, you can connect them to your computer or, using the wireless NFC technology, simply hold the key close to your device to transmit the factor.
Useful Features
Now, let’s finally talk about how to use it. I am going to talk about the following features:
- 2-factor authentication (2FA)
- Web Authentication (WebAuthn, also FIDO2)
- Encrypt and Sign emails with PGP
- Leave a secret message on your YubiKey
There are several more services that YubiKey supports, but these are the ones I really felt useful for my day-to-day use. If you have more cool use-cases, drop a message below this post!
2-Factor Authentication
The intended use-case for YubiKey: Authentication! Many services already support it, and you can often find the 2FA option in the Security settings of your favorite services, such as Google (Mail), Microsoft, and Apple. For developers, it might also be interesting to know that GitHub and GitLab both offer to use one or more YubiKeys as a second factor.
Yubico (the company behind YubiKey) provides a full list of supported services on their website: https://www.yubico.com/works-with-yubikey/catalog/
Web Authentication
WebAuthn and FIDO2 are modern security standards that enable passwordless authentication for online services, making it more secure and convenient to log in by using biometrics or hardware tokens like YubiKeys. This means that you can log in to supported services using only your YubiKey. This does not make your account more secure, but provides an alternative way to quickly log into a service without needing your password manager. Overall, a convenient feature for the user.
Services I found that allow to register a hardware key for authentication are: Nextcloud, Google, Facebook, Twitter/X, or GitHub.
OpenPGP and YubiKey
Did you know that a YubiKey is also a smart card? Smart cards are credit-card-sized devices that store and process information securely, often used for authentication and access control. What has this to do with OpenPGP, the open-source encryption standard?
Warning: the following requires some advanced knowledge and technical know-how to perform, so it might not be for everyone!
At first glance, these are different concepts. OpenPGP, which is primarily used for secure email communication, uses one or several cryptographic keys to allow people to send you encrypted mails. Also, you can sign emails so that other people can verify that you sent them, and not some impersonator.
Now, even though you can generate keys on the YubiKey to be used with PGP, it is recommended that you generate them externally and then copy them to the YubiKey. In this way, you can extract and backup your keys in case you lose the YubiKey. The official guide (archive link) to generate OpenPGP keys and/or copy existing keys to the YubiKey explains the process, but you can also find an advanced tutorial in this guide (archive link).
Now, if you read through the guides, you might find that you need to push your crypto keys on the YubiKey using the keytocard command. This is because we are actually using the Smartcard feature of YubiKey to store the keys!
How does it work in practice? After setting up the YubiKey, you can delete the private keys on your computer (do not forget to backup) and, if you are using GPG, also delete them from the gpg keyring. Then, load the key into your favorite email program (mine is Thunderbird) to be used when you compose new mails. I tend to enable email signing by default, such that every mail I send includes a proof that I sent it.
Now, whenever you send a signed email or receive an encrypted email, you simply need to connect your YubiKey and press the button on the hardware key to sign or decrypt an email. If you set a PIN for your YubiKey (highly recommended), you also need to provide it.
The best part of this feature is: It may even work on mobile! I use K-9 Mail and OpenKeychain, which allows me to use all the PGP features I need. Even if I lose my phone, the keys are safely stored on the YubiKey (which I carry separately), so whoever finds my phone at least cannot read my encrypted mails (whew, what a relief, huh?).
As a side note: If your device does not support NFC, you need to buy a YubiKey with an appropriate connector (probably USB-C or Apple’s Lightning) or you cannot use it with your phone.
A (secret) message
This is more of a gimmick, I admit, but I thought about what happens if I ever lose the key. I would love to have it back, but how to communicate to a potential finder how to contact you?
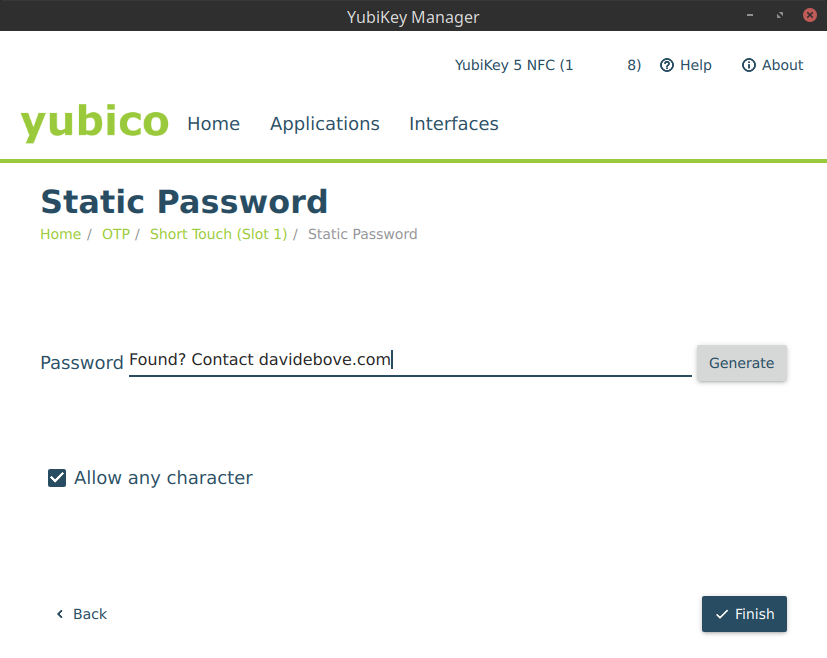
YubiKey allows configuring a “static password†that is emitted when you press the button on the YubiKey. When it is connected to a device, the YubiKey acts as a keyboard, so whenever you press the hardware button, the static password is entered as if someone entered it manually.
Now, I don’t think it is safe to use the feature to store a real password, as anyone (e.g., your coworkers) could “borrow†the key, connect them to their computer, open their notepad and get the password. My static password is a bit different: It contains the following message:
So, if an honest person finds the YubiKey and manages to connect it, they might see the message and contact me about it.
You can use the YubiKey Manager to set the message. Go to Applications → OTP and configure a “static password†for either a “short touch†or a “long touch†(or both).
This is it for today! There might be more uses for a hardware key like YubiKey, but I found the above features to be the most useful to me. If you agree, leave a comment, and if you disagree, tell me what cool features I missed!
Photo by Andy Kennedy on Unsplash

Be First to Comment